- India never invaded any country in her last 100000 years of history.
- When many cultures were only nomadic forest dwellers over 5000 years ago, Indians established Harappan culture in Sindhu Valley (Indus Valley Civilization)
- The name 'India' is derived from the River Indus, the valleys around which were the home of the early settlers. The Aryan worshippers referred to the river Indus as the Sindhu.
- The Persian invaders converted it into Hindu. The name 'Hindustan' combines Sindhu and Hindu and thus refers to the land of the Hindus.
- Chess was invented in India.
- Algebra, Trigonometry and Calculus are studies, which originated in India.
- The 'Place Value System' and the 'Decimal System' were developed in India in 100 B.C.
- The World's First Granite Temple is the Brihadeswara Temple at Tanjavur, Tamil Nadu. The shikhara of the temple is made from a single 80-tonne piece of granite. This magnificent temple was built in just five years, (between 1004 AD and 1009 AD) during the reign of Rajaraja Chola.
- India is the largest democracy in the world, the 6th largest Country in the world, and one of the most ancient civilizations.
- The game of Snakes & Ladders was created by the 13th century poet saint Gyandev. It was originally called 'Mokshapat'. The ladders in the game represented virtues and the snakes indicated vices. The game was played with cowrie shells and dices. In time, the game underwent several modifications, but its meaning remained the same, i.e. good deeds take people to heaven and evil to a cycle of re-births.
- The world's highest cricket ground is in Chail, Himachal Pradesh. Built in 1893 after leveling a hilltop, this cricket pitch is 2444 meters above sea level.
- India has the largest number of Post Offices in the world.
- The largest employer in the world is the Indian Railways, employing over a million people.
- The world's first university was established in Takshila in 700 BC. More than 10,500 students from all over the world studied more than 60 subjects. The University of Nalanda built in the 4th century was one of the greatest achievements of ancient India in the field of education.
- Ayurveda is the earliest school of medicine known to mankind. The Father of Medicine, Charaka, consolidated Ayurveda 2500 years ago.
- India was one of the richest countries till the time of British rule in the early 17th Century. Christopher Columbus, attracted by India's wealth, had come looking for a sea route to India when he discovered America by mistake.
- The Art of Navigation & Navigating was born in the river Sindh over 6000 years ago. The very word Navigation is derived from the Sanskrit word 'NAVGATIH'. The word navy is also derived from the Sanskrit word 'Nou'.
- Bhaskaracharya rightly calculated the time taken by the earth to orbit the Sun hundreds of years before the astronomer Smart. According to his calculation, the time taken by the Earth to orbit the Sun was 365.258756484 days.
- The value of "pi" was first calculated by the Indian Mathematician Budhayana, and he explained the concept of what is known as the Pythagorean Theorem. He discovered this in the 6th century, long before the European mathematicians.
- Algebra, Trigonometry and Calculus also originated in India.Quadratic Equations were used by Sridharacharya in the 11th century. The largest numbers the Greeks and the Romans used were 106 whereas Hindus used numbers as big as 10*53 (i.e. 10 to the power of 53) with specific names as early as 5000 B.C.during the Vedic period.Even today, the largest used number is Terra: 10*12(10 to the power of 12).
- Until 1896, India was the only source of diamonds in the world
(Source: Gemological Institute of America). - The Baily Bridge is the highest bridge in the world. It is located in the Ladakh valley between the Dras and Suru rivers in the Himalayan mountains. It was built by the Indian Army in August 1982.
- Sushruta is regarded as the Father of Surgery. Over2600 years ago Sushrata & his team conducted complicated surgeries like cataract, artificial limbs, cesareans, fractures, urinary stones, plastic surgery and brain surgeries.
- Usage of anaesthesia was well known in ancient Indian medicine. Detailed knowledge of anatomy, embryology, digestion, metabolism,physiology, etiology, genetics and immunity is also found in many ancient Indian texts.
- India exports software to 90 countries.
- The four religions born in India - Hinduism, Buddhism, Jainism, and Sikhism, are followed by 25% of the world's population.
- Jainism and Buddhism were founded in India in 600 B.C. and 500 B.C. respectively.
- Islam is India's and the world's second largest religion.
- There are 300,000 active mosques in India, more than in any other country, including the Muslim world.
- The oldest European church and synagogue in India are in the city of Cochin. They were built in 1503 and 1568 respectively.
- Jews and Christians have lived continuously in India since 200 B.C. and 52 A.D. respectively
- The largest religious building in the world is Angkor Wat, a Hindu Temple in Cambodia built at the end of the 11th century.
- The Vishnu Temple in the city of Tirupathi built in the 10th century, is the world's largest religious pilgrimage destination. Larger than either Rome or Mecca, an average of 30,000 visitors donate $6 million (US) to the temple everyday.
- Sikhism originated in the Holy city of Amritsar in Punjab. Famous for housing the Golden Temple, the city was founded in 1577.
- Varanasi, also known as Benaras, was called "the Ancient City" when Lord Buddha visited it in 500 B.C., and is the oldest, continuously inhabited city in the world today.
- India provides safety for more than 300,000 refugees originally from Sri Lanka, Tibet, Bhutan, Afghanistan and Bangladesh, who escaped to flee religious and political persecution.
- His Holiness, the Dalai Lama, the exiled spiritual leader of Tibetan Buddhists, runs his government in exile from Dharmashala in northern India.
- Martial Arts were first created in India, and later spread to Asia by Buddhist missionaries.
- Yoga has its origins in India and has existed for over 5,000 years.
Wednesday, December 30, 2009
Interesting Facts about India
Thursday, December 17, 2009
Collaborative Computing & The Internet
Traditional Collaboration – Groupware & Computer-Supported Cooperative Work
Internet Culture
Internet Congestion Control
1.1 What is congestion?2. Present technology.
1.2 Congestion collapse.
1.3 Controlling congestion: design considerations.
1.4 Implicit feedback.
1.5 Source behaviour with binary feedback.
1.6 Stability.
1.7 Rate-based versus window-based control.
1.8 RTT estimation.
1.9 Traffic phase effects.
1.10 Queue management.
1.11 Scalability.
1.12 Explicit feedback.
1.13 Special environments.
1.14 Congestion control and OSI layers.
1.15 Multicast congestion control.
1.16 Incentive issues.
1.17 Fairness.
1.18 Conclusion.
2.1 Introducing TCP.
2.2 TCP window management.
2.3 TCP RTO calculation.
2.4 TCP congestion control and reliability.
2.5 Concluding remarks about TCP.
2.6 The Stream Control Transmission Protocol (SCTP).
2.7 Random Early Detection (RED).
2.8 The ATM‘Available Bit Rate’ service.
Internet Congestion
Internet refers to network of networks, so the network congestion is the situation in which an increase in data transmission than the network devices (routers and switches) can accommodate. This results in a proportionately reductions, in throughput.
Throughput is the amount of data that passes through the network per unit of time, such as the number of packets per second.
Packets are the fundamental unit of data transmission on the internet and all other TCP/IP networks, including most LANs.
For this we need buffer, buffer is a portion of a device’s memory that is set aside as a temporary holding place for data that is being sent to or received from another device. This ca result in delayed of lost packets, thus causing applications to retransmit the data, thereby adding more traffic and further increasing the congestion.
Congestion Collapse is the situation in which the congestion becomes so great that throughput drops to a low level and thus little useful communication occurs. It can be stable state with the same intrinsic load level that would by itself not produce congestion. This is because it is caused by the aggressive retransmission used by carious network protocols to compensate for the packet loss that occurs as a result of congestion, a retransmission that continues even after the load is reduced to a level that would not have induced congestion by itself.
Congestion Control
It is the process that is used to reduce congestion in a network. This includes making decisions such as: deciding when to accept new TRAFFIC, when to delete packets and when to adjust the ROUTING policies used in a network.
Network congestion is somewhat analogues to road congestion. One technique that has been used with some success to deal with road congestion is monitoring, in which rate of vehicles entering a road or area is restricted by signals.
The area of Internet congestion control was baptised in 1986-1987 when the then ARPANET suffered ‘congestion collapse’. Congestion collapse had been predicted by Nagel [89] in 1984. Congestion collapse occurs when mounting levels of traffic result in high packet loss inside the network, such that few or no packets are actually delivered to their destination, yet each link is highly loaded.
Various techniques have likewise been developed in attempt to minimize congestion collapse in communications networks.
1) Load control mechanisms
When the capacity available is less than the demand for capacity, load control is the critical element which determines how many packets are allowed onto each link of the network, who gets to send them and when.
At one end of the spectrum are the connection admission control (CAC) schemes, such as the Resource Reservation Protocol (RSVP) [4]. Such schemes require the network to maintain information about each connection and arbitrate whether connections are admitted or rejected so that the connections that are admitted can be absolutely guaranteed their required bandwidth for the duration of the connection. When the load of requested connections is increased beyond the capacity of the network then some new users will be rejected in order to maintain the bandwidth guarantees made to already admit users. CAC is good for honoring bandwidth supply contracts that specify minimum rates.
2) Rethinking Best-Effort Networks
To introduce Kelly’s framework for describing best-effort networks, we will provide an example of how bandwidth allocation in a best effort network compares to bandwidth allocation in a CAC network. Let us consider an example where there are three users each requesting a 1 Mb/s connection across the same 2 Mb/s link. In a CAC network, one user will have to miss out. However, the best-effort network makes this situation less rigid by making the users’ demand for bandwidth elastic. When users do not need strict guarantees of minimum bandwidth then blocking one user is not necessarily the best solution possible. Let us assume that a user is able to quantify, by a single number, its perceived quality of service (QoS) value of sending at a certain rate. Say, transmitting at a rate of 1 Mb/s gives the maximum possible user perceived QoS value, but transmitting at a rate of less than 1 Mb/s still gives some, but less, QoS value to the user. Then, it is possible to conceive of a solution, where by making the three users transmit at 2/3 Mb/s each, the sum of the perceived QoS values of all three users is greater than the sum if only two users are allowed to transmit at the maximum 1 Mb/s and one user is blocked. In such a system, where the user demand has some flexibility, it is possible to achieve a compromise solution for sharing the available capacity which is better for the QoS of the whole community of users, despite giving less capacity to some users. This is exactly the solution that the best-effort network achieves.
3) Supply Demand Pricing
Fix the price as pay per bit.
4) Differentiated Bandwidth
Differentiate bandwidth according to the demand and price rule. More demand more price less demand less price.
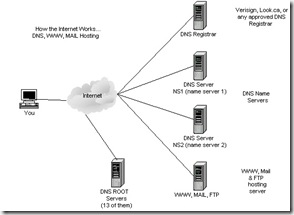
How Internet Works
One of the greatest things about the Internet is that nobody really owns it. It is a global collection of networks, both big and small. These networks connect together in many different ways to form the single entity that we know as the Internet. In fact, the very name comes from this idea of interconnected networks.
Since its beginning in 1969, the Internet has grown from four host computer systems to tens of millions. However, just because nobody owns the Internet, it doesn't mean it is not monitored and maintained in different ways. The Internet Society, a non-profit group established in 1992, oversees the formation of the policies and protocols that define how we use and interact with the Internet.
The Internet: Computer Network Hierarchy
Every computer that is connected to the Internet is part of a network, even the one in your home. For example, you may use a modem and dial a local number to connect to an Internet Service Provider (ISP). At work, you may be part of a local area network (LAN), but you most likely still connect to the Internet using an ISP that your company has contracted with. When you connect to your ISP, you become part of their network. The ISP may then connect to a larger network and become part of their network. The Internet is simply a network of networks.
Most large communications companies have their own dedicated backbones connecting various regions. In each region, the company has a Point of Presence (POP). The POP is a place for local users to access the company's network, often through a local phone number or dedicated line. The amazing thing here is that there is no overall controlling network. Instead, there are several high-level networks connecting to each other through Network Access Points or NAPs.

When you connect to the Internet, your computer
becomes part of a network.
Multipurpose Internet Mail Extensions
MIME (Multipurpose Internet Mail Extensions) is an Internet standard for describes message content types.
MIME is a standard for describing different types of information This was originally meant to be used to specify encoding for different types of information into text. This made it possible to send them as e-mail.
The standard MIME is also used in other types of communication where there is a need for specifying which type of information is used. This could be your local operating system or a web server.
MIME defines mechanisms for sending other kinds of information in e-mail. These include text in languages other than English using character encodings other than ASCII, and 8-bit binary content such as files containing images, sounds, movies, and computer programs. MIME is also a fundamental component of communication protocols such as HTTP, which requires that data be transmitted in the context of e-mail-like messages even though the data might not (and usually doesn't) actually have anything to do with e-mail. Mapping messages into and out of MIME format is typically done automatically by an e-mail client or by mail servers when sending or receiving Internet (SMTP/MIME) e-mail.
How do I read MIME in my mail?
Mime is just a specification. Normally the information is encoded with some other standard format. When decoded it regains it original shape.
To be able to read the file you need an application that can handle the attached file. If two files, a word document and a image is sent by email they would both get encoded as mime. Upon receiving these files there need to be an application associated with each file type. Microsoft word or maybe another word processor would be associated with the word document making it possible to read the file. Photoshop or another image viewer would be associated with the image.
Normally the conversion from MIME to files is handled by the e-mail application. When the file is stored on disk it is up to the operating system to map an application to file type.
MIME messages can contain text, images, audio, video, and other application-specific data.
Official MIME info is provided by the Internet Engineering Task Force (IETF) in the following documents:
- RFC-822 Standard for ARPA Internet text messages
- RFC-2045 MIME Part 1: Format of Internet Message Bodies
- RFC-2046 MIME Part 2: Media Types
- RFC-2047 MIME Part 3: Header Extensions for Non-ASCII Text
- RFC-2048 MIME Part 4: Registration Procedures
- RFC-2049 MIME Part 5: Conformance Criteria and Examples
Different applications support different MIME types.
The reference below is a list of MIME types supported by Microsoft Internet Information Server version 5.
MIME Types
MIME Types (Application):
| Type/sub-type | Extension |
| application/envoy | evy |
| application/fractals | fif |
| application/futuresplash | spl |
| application/hta | hta |
| application/internet-property-stream | acx |
| application/mac-binhex40 | hqx |
| application/msword | doc |
| application/msword | dot |
| application/octet-stream | * |
| application/octet-stream | bin |
| application/octet-stream | class |
| application/octet-stream | dms |
| application/octet-stream | exe |
| application/octet-stream | lha |
| application/octet-stream | lzh |
| application/oda | oda |
| application/olescript | axs |
| application/pdf | |
| application/pics-rules | prf |
| application/pkcs10 | p10 |
| application/pkix-crl | crl |
| application/postscript | ai |
| application/postscript | eps |
| application/postscript | ps |
| application/rtf | rtf |
| application/set-payment-initiation | setpay |
| application/set-registration-initiation | setreg |
| application/vnd.ms-excel | xla |
| application/vnd.ms-excel | xlc |
| application/vnd.ms-excel | xlm |
| application/vnd.ms-excel | xls |
| application/vnd.ms-excel | xlt |
| application/vnd.ms-excel | xlw |
| application/vnd.ms-outlook | msg |
| application/vnd.ms-pkicertstore | sst |
| application/vnd.ms-pkiseccat | cat |
| application/vnd.ms-pkistl | stl |
| application/vnd.ms-powerpoint | pot |
| application/vnd.ms-powerpoint | pps |
| application/vnd.ms-powerpoint | ppt |
| application/vnd.ms-project | mpp |
| application/vnd.ms-works | wcm |
| application/vnd.ms-works | wdb |
| application/vnd.ms-works | wks |
| application/vnd.ms-works | wps |
| application/winhlp | hlp |
| application/x-bcpio | bcpio |
| application/x-cdf | cdf |
| application/x-compress | z |
| application/x-compressed | tgz |
| application/x-cpio | cpio |
| application/x-csh | csh |
| application/x-director | dcr |
| application/x-director | dir |
| application/x-director | dxr |
| application/x-dvi | dvi |
| application/x-gtar | gtar |
| application/x-gzip | gz |
| application/x-hdf | hdf |
| application/x-internet-signup | ins |
| application/x-internet-signup | isp |
| application/x-iphone | iii |
| application/x-javascript | js |
| application/x-latex | latex |
| application/x-msaccess | mdb |
| application/x-mscardfile | crd |
| application/x-msclip | clp |
| application/x-msdownload | dll |
| application/x-msmediaview | m13 |
| application/x-msmediaview | m14 |
| application/x-msmediaview | mvb |
| application/x-msmetafile | wmf |
| application/x-msmoney | mny |
| application/x-mspublisher | pub |
| application/x-msschedule | scd |
| application/x-msterminal | trm |
| application/x-mswrite | wri |
| application/x-netcdf | cdf |
| application/x-netcdf | nc |
| application/x-perfmon | pma |
| application/x-perfmon | pmc |
| application/x-perfmon | pml |
| application/x-perfmon | pmr |
| application/x-perfmon | pmw |
| application/x-pkcs12 | p12 |
| application/x-pkcs12 | pfx |
| application/x-pkcs7-certificates | p7b |
| application/x-pkcs7-certificates | spc |
| application/x-pkcs7-certreqresp | p7r |
| application/x-pkcs7-mime | p7c |
| application/x-pkcs7-mime | p7m |
| application/x-pkcs7-signature | p7s |
| application/x-sh | sh |
| application/x-shar | shar |
| application/x-shockwave-flash | swf |
| application/x-stuffit | sit |
| application/x-sv4cpio | sv4cpio |
| application/x-sv4crc | sv4crc |
| application/x-tar | tar |
| application/x-tcl | tcl |
| application/x-tex | tex |
| application/x-texinfo | texi |
| application/x-texinfo | texinfo |
| application/x-troff | roff |
| application/x-troff | t |
| application/x-troff | tr |
| application/x-troff-man | man |
| application/x-troff-me | me |
| application/x-troff-ms | ms |
| application/x-ustar | ustar |
| application/x-wais-source | src |
| application/x-x509-ca-cert | cer |
| application/x-x509-ca-cert | crt |
| application/x-x509-ca-cert | der |
| application/ynd.ms-pkipko | pko |
| application/zip | zip |
MIME Types (Audio):
| Type/sub-type | Extension |
| audio/basic | au |
| audio/basic | snd |
| audio/mid | mid |
| audio/mid | rmi |
| audio/mpeg | mp3 |
| audio/x-aiff | aif |
| audio/x-aiff | aifc |
| audio/x-aiff | aiff |
| audio/x-mpegurl | m3u |
| audio/x-pn-realaudio | ra |
| audio/x-pn-realaudio | ram |
| audio/x-wav | wav |
MIME Types (Image):
| Type/sub-type | Extension |
| image/bmp | bmp |
| image/cis-cod | cod |
| image/gif | gif |
| image/ief | ief |
| image/jpeg | jpe |
| image/jpeg | jpeg |
| image/jpeg | jpg |
| image/pipeg | jfif |
| image/svg+xml | svg |
| image/tiff | tif |
| image/tiff | tiff |
| image/x-cmu-raster | ras |
| image/x-cmx | cmx |
| image/x-icon | ico |
| image/x-portable-anymap | pnm |
| image/x-portable-bitmap | pbm |
| image/x-portable-graymap | pgm |
| image/x-portable-pixmap | ppm |
| image/x-rgb | rgb |
| image/x-xbitmap | xbm |
| image/x-xpixmap | xpm |
| image/x-xwindowdump | xwd |
MIME Types (Message):
| Type/sub-type | Extension |
| message/rfc822 | mht |
| message/rfc822 | mhtml |
| message/rfc822 | nws |
MIME Types (Text):
| Type/sub-type | Extension |
| text/css | css |
| text/h323 | 323 |
| text/html | htm |
| text/html | html |
| text/html | stm |
| text/iuls | uls |
| text/plain | bas |
| text/plain | c |
| text/plain | h |
| text/plain | txt |
| text/richtext | rtx |
| text/scriptlet | sct |
| text/tab-separated-values | tsv |
| text/webviewhtml | htt |
| text/x-component | htc |
| text/x-setext | etx |
| text/x-vcard | vcf |
MIME Types (Video):
| Type/sub-type | Extension |
| video/mpeg | mp2 |
| video/mpeg | mpa |
| video/mpeg | mpe |
| video/mpeg | mpeg |
| video/mpeg | mpg |
| video/mpeg | mpv2 |
| video/quicktime | mov |
| video/quicktime | qt |
| video/x-la-asf | lsf |
| video/x-la-asf | lsx |
| video/x-ms-asf | asf |
| video/x-ms-asf | asr |
| video/x-ms-asf | asx |
| video/x-msvideo | avi |
| video/x-sgi-movie | movie |
MIME Types (Video):
| Type/sub-type | Extension |
| x-world/x-vrml | flr |
| x-world/x-vrml | vrml |
| x-world/x-vrml | wrl |
| x-world/x-vrml | wrz |
| x-world/x-vrml | xaf |
| x-world/x-vrml | xof |
Mime Types By File Extension
| Extension | Type/sub-type |
| application/octet-stream | |
| 323 | text/h323 |
| acx | application/internet-property-stream |
| ai | application/postscript |
| aif | audio/x-aiff |
| aifc | audio/x-aiff |
| aiff | audio/x-aiff |
| asf | video/x-ms-asf |
| asr | video/x-ms-asf |
| asx | video/x-ms-asf |
| au | audio/basic |
| avi | video/x-msvideo |
| axs | application/olescript |
| bas | text/plain |
| bcpio | application/x-bcpio |
| bin | application/octet-stream |
| bmp | image/bmp |
| c | text/plain |
| cat | application/vnd.ms-pkiseccat |
| cdf | application/x-cdf |
| cer | application/x-x509-ca-cert |
| class | application/octet-stream |
| clp | application/x-msclip |
| cmx | image/x-cmx |
| cod | image/cis-cod |
| cpio | application/x-cpio |
| crd | application/x-mscardfile |
| crl | application/pkix-crl |
| crt | application/x-x509-ca-cert |
| csh | application/x-csh |
| css | text/css |
| dcr | application/x-director |
| der | application/x-x509-ca-cert |
| dir | application/x-director |
| dll | application/x-msdownload |
| dms | application/octet-stream |
| doc | application/msword |
| dot | application/msword |
| dvi | application/x-dvi |
| dxr | application/x-director |
| eps | application/postscript |
| etx | text/x-setext |
| evy | application/envoy |
| exe | application/octet-stream |
| fif | application/fractals |
| flr | x-world/x-vrml |
| gif | image/gif |
| gtar | application/x-gtar |
| gz | application/x-gzip |
| h | text/plain |
| hdf | application/x-hdf |
| hlp | application/winhlp |
| hqx | application/mac-binhex40 |
| hta | application/hta |
| htc | text/x-component |
| htm | text/html |
| html | text/html |
| htt | text/webviewhtml |
| ico | image/x-icon |
| ief | image/ief |
| iii | application/x-iphone |
| ins | application/x-internet-signup |
| isp | application/x-internet-signup |
| jfif | image/pipeg |
| jpe | image/jpeg |
| jpeg | image/jpeg |
| jpg | image/jpeg |
| js | application/x-javascript |
| latex | application/x-latex |
| lha | application/octet-stream |
| lsf | video/x-la-asf |
| lsx | video/x-la-asf |
| lzh | application/octet-stream |
| m13 | application/x-msmediaview |
| m14 | application/x-msmediaview |
| m3u | audio/x-mpegurl |
| man | application/x-troff-man |
| mdb | application/x-msaccess |
| me | application/x-troff-me |
| mht | message/rfc822 |
| mhtml | message/rfc822 |
| mid | audio/mid |
| mny | application/x-msmoney |
| mov | video/quicktime |
| movie | video/x-sgi-movie |
| mp2 | video/mpeg |
| mp3 | audio/mpeg |
| mpa | video/mpeg |
| mpe | video/mpeg |
| mpeg | video/mpeg |
| mpg | video/mpeg |
| mpp | application/vnd.ms-project |
| mpv2 | video/mpeg |
| ms | application/x-troff-ms |
| mvb | application/x-msmediaview |
| nws | message/rfc822 |
| oda | application/oda |
| p10 | application/pkcs10 |
| p12 | application/x-pkcs12 |
| p7b | application/x-pkcs7-certificates |
| p7c | application/x-pkcs7-mime |
| p7m | application/x-pkcs7-mime |
| p7r | application/x-pkcs7-certreqresp |
| p7s | application/x-pkcs7-signature |
| pbm | image/x-portable-bitmap |
| | application/pdf |
| pfx | application/x-pkcs12 |
| pgm | image/x-portable-graymap |
| pko | application/ynd.ms-pkipko |
| pma | application/x-perfmon |
| pmc | application/x-perfmon |
| pml | application/x-perfmon |
| pmr | application/x-perfmon |
| pmw | application/x-perfmon |
| pnm | image/x-portable-anymap |
| pot, | application/vnd.ms-powerpoint |
| ppm | image/x-portable-pixmap |
| pps | application/vnd.ms-powerpoint |
| ppt | application/vnd.ms-powerpoint |
| prf | application/pics-rules |
| ps | application/postscript |
| pub | application/x-mspublisher |
| qt | video/quicktime |
| ra | audio/x-pn-realaudio |
| ram | audio/x-pn-realaudio |
| ras | image/x-cmu-raster |
| rgb | image/x-rgb |
| rmi | audio/mid |
| roff | application/x-troff |
| rtf | application/rtf |
| rtx | text/richtext |
| scd | application/x-msschedule |
| sct | text/scriptlet |
| setpay | application/set-payment-initiation |
| setreg | application/set-registration-initiation |
| sh | application/x-sh |
| shar | application/x-shar |
| sit | application/x-stuffit |
| snd | audio/basic |
| spc | application/x-pkcs7-certificates |
| spl | application/futuresplash |
| src | application/x-wais-source |
| sst | application/vnd.ms-pkicertstore |
| stl | application/vnd.ms-pkistl |
| stm | text/html |
| svg | image/svg+xml |
| sv4cpio | application/x-sv4cpio |
| sv4crc | application/x-sv4crc |
| swf | application/x-shockwave-flash |
| t | application/x-troff |
| tar | application/x-tar |
| tcl | application/x-tcl |
| tex | application/x-tex |
| texi | application/x-texinfo |
| texinfo | application/x-texinfo |
| tgz | application/x-compressed |
| tif | image/tiff |
| tiff | image/tiff |
| tr | application/x-troff |
| trm | application/x-msterminal |
| tsv | text/tab-separated-values |
| txt | text/plain |
| uls | text/iuls |
| ustar | application/x-ustar |
| vcf | text/x-vcard |
| vrml | x-world/x-vrml |
| wav | audio/x-wav |
| wcm | application/vnd.ms-works |
| wdb | application/vnd.ms-works |
| wks | application/vnd.ms-works |
| wmf | application/x-msmetafile |
| wps | application/vnd.ms-works |
| wri | application/x-mswrite |
| wrl | x-world/x-vrml |
| wrz | x-world/x-vrml |
| xaf | x-world/x-vrml |
| xbm | image/x-xbitmap |
| xla | application/vnd.ms-excel |
| xlc | application/vnd.ms-excel |
| xlm | application/vnd.ms-excel |
| xls | application/vnd.ms-excel |
| xlt | application/vnd.ms-excel |
| xlw | application/vnd.ms-excel |
| xof | x-world/x-vrml |
| xpm | image/x-xpixmap |
| xwd | image/x-xwindowdump |
| z | application/x-compress |
| zip | application/zip |
MIME Technical Summary
MIME is defined by an Internet standard document called RFC1521. This document summarizes the contents of RFC1521. Sufficient detail is presented here to understand the capabilities of MIME. For sufficient detail to implement MIME please read RFC1521.
MIME allows messages to contain multiple objects. When multiple objects are in a MIME message, they are represented in a form called a body part. A body part has a header and a body, so it makes sense to speak about the body of a body part. Also, body parts can be nested in bodies that contain one or multiple body parts.
The Content-Type values, subtypes, and parameter names defined in the MIME standard are case-insensitive. However, many parameter values are case sensitive
The MIME standard is written to allow MIME to be extended in certain ways, without having to revise the standard. MIME specifies sets of values that are allowed for various fields and parameters. The provides a procedure for extending these sets of values by registering them with an entity called the Internet Assigned Numbers Authority (IANA).
Wednesday, December 16, 2009
Graph & Tree
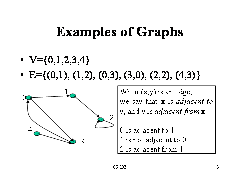
• A graph is a finite set of nodes with edges between nodes
• Formally, a graph G is a structure (V,E) consisting of
– a finite set V called the set of nodes, and
– a set E that is a subset of VxV. That is, E is a set of pairs of the form (x,y) where x and y are nodes in V
Graph Representation
• For graphs to be computationally useful, they have to be conveniently represented in programs
• There are two computer representations of graphs:
– Adjacency matrix representation
– Adjacency lists representation
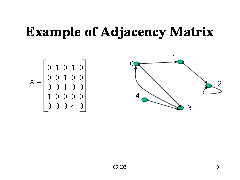
Adjacency Matrix Representation
• In this representation, each graph of n nodes is represented by an n x n matrix A, that is, a two-dimensional array A
• The nodes are (re)-labeled 1,2,…,n
• A[i][j] = 1 if (i,j) is an edge
• A[i][j] = 0 if (i,j) is not an edge
Pros and Cons of Adjacency Matrices
• Pros:
– Simple to implement
– Easy and fast to tell if a pair (i,j) is an edge: simply check if A[i][j] is 1 or 0
• Cons:
– No matter how few edges the graph has, the matrix takes O(n2) in memory
Adjacency Lists Representation
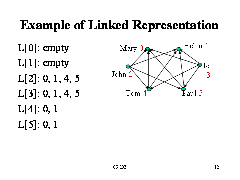
• A graph of n nodes is represented by a one-dimensional array L of linked lists, where
– L[i] is the linked list containing all the nodes adjacent from node i.
– The nodes in the list L[i] are in no particular order
Pros and Cons of Adjacency Lists
• Pros:
– Saves on space (memory): the representation takes as many memory words as there are nodes and edge.
• Cons:
– It can take up to O(n) time to determine if a pair of nodes (i,j) is an edge: one would have to search the linked list L[i], which takes time proportional to the length of L[i].
Graph Traversal Techniques
• The previous connectivity problem, as well as many other graph problems, can be solved using graph traversal techniques
• There are two standard graph traversal techniques:
– Depth-First Search (DFS)
– Breadth-First Search (BFS)
• In both DFS and BFS, the nodes of the undirected graph are visited in a systematic manner so that every node is visited exactly one.
• Both BFS and DFS give rise to a tree:
– When a node x is visited, it is labeled as visited, and it is added to the tree
– If the traversal got to node x from node y, y is viewed as the parent of x, and x a child of y
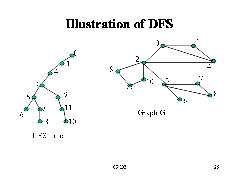
Depth-First Search
• DFS follows the following rules:
1. Select an unvisited node x, visit it, and treat as the current node
2. Find an unvisited neighbor of the current node, visit it, and make it the new current node;
3. If the current node has no unvisited neighbors, backtrack to the its parent, and make that parent the new current node;
4. Repeat steps 3 and 4 until no more nodes can be visited.
5. If there are still unvisited nodes, repeat from step 1.
Implementation of DFS
• Observations:
– the last node visited is the first node from which to proceed.
– Also, the backtracking proceeds on the basis of "last visited, first to backtrack too".
– This suggests that a stack is the proper data structure to remember the current node and how to backtrack.
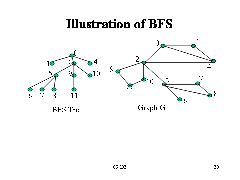
Breadth-First Search
• BFS follows the following rules:
1. Select an unvisited node x, visit it, have it be the root in a BFS tree being formed. Its level is called the current level.
2. From each node z in the current level, in the order in which the level nodes were visited, visit all the unvisited neighbors of z. The newly visited nodes from this level form a new level that becomes the next current level.
3. Repeat step 2 until no more nodes can be visited.
4. If there are still unvisited nodes, repeat from Step 1.
Implementation of DFS
• Observations:
– the first node visited in each level is the first node from which to proceed to visit new nodes.
• This suggests that a queue is the proper data structure to remember the order of the steps.
Thursday, December 10, 2009
WAP for paramid pattern-2
WAP to generate the peramid pattern
Output:-
121
12321
1234321
123454321
Solution:-
#include
#include
void main()
{
int i,j;
for (i=1;i<=5;i++) { for(j=4;j>=i;j--)
{
printf(" ");
}
for(j=1;j<=i;j++) { printf("%d",j); } printf("\n"); } getch(); }