The first computer firewall was a non routing UNIX host with connections to two different networks. One network card connected to the Internet and the other to the private LAN. To reach the Internet from the private network, you had to logon to the firewall (Unix) server. You then used the resources of the system to access the Internet. For example, you could use X−windows to run Netscape's browser on the firewall system and have the display on your work station. With the browser running on the firewall it has access to both networks.
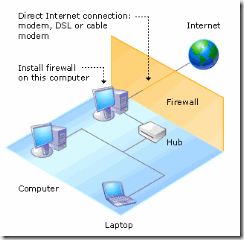
Firewall Politics
You shouldn't believe a firewall machine is all you need. Set policies first. Firewalls are used for two purposes.
1. to keep people (worms / crackers) out.
2. to keep people (employees / children) in.

Create a security policy is simple.
1. describe what you need to service
2. describe the group of people you need to service
3. describe which service each group needs access to
4. for each service group describe how the service should be keep secure
5. write a statment making all other forms of access a vialation
Types of Firewalls
There are two types of firewalls.1. Filtering Firewalls − that block selected network packets.
2. Proxy Servers (sometimes called firewalls) − that make network connections for you.
Packet Filtering Firewalls
Packet Filtering is the type of firewall built into the Linux kernel.A filtering firewall works at the network level. Data is only allowed to leave the system if the firewall rules allow it. As packets arrive they are filtered by their type, source address, destination address, and port information contained in each packet.
Filtering firewalls do not provide for password controls. User can not identify themselves. The only identity a user has is the IP number assigned to their workstation. This can be a problem if you are going to use DHCP (Dynamic IP assignments). This is because rules are based on IP numbers you will have to adjust the rules as new IP numbers are assigned.
Proxy Servers
Proxies are mostly used to control, or monitor, outbound traffic. Some application proxies cache therequested data. This lowers bandwidth requirements and decreases the access the same data for the next user. It also gives unquestionable evidence of what was transferred.
There are two types of proxy servers.
1. Application Proxies − that do the work for you.
2. SOCKS Proxies − that cross wire ports.
Application Proxy
The best example is a person telneting to another computer and then telneting from there to the outside world. With a application proxy server the process is automated. As you telnet to the outside world the client send you to the proxy first. The proxy then connects to the server you requested (the outside world) and returns the data to you.Because proxy servers are handling all the communications, they can log everything they (you) do. For HTTP (web) proxies this includes very URL they you see. For FTP proxies this includes every file you download. They can even filter out "inappropriate" words from the sites you visit or scan for viruses.
Application proxy servers can authenticate users. Before a connection to the outside is made, the server can ask the user to login first. To a web user this would make every site look like it required a login.
SOCKS Proxy
A SOCKS server is a lot like an old switch board. It simply cross wires your connection through the system to another outside connection.Most SOCKS server only work with TCP type connections. And like filtering firewalls they don't provide for user authentication. They can however record where each user connected to.
No comments:
Post a Comment